The SMB Guide to Implementing Zero Trust Security on a Budget

In today’s digital landscape, cybersecurity threats don’t discriminate based on company size. Small businesses across North Texas are increasingly targeted by sophisticated attacks, yet many believe implementing robust security frameworks like Zero Trust is beyond their budget. At RZR Solutions, we’re here to dispel that myth.
Zero Trust security operates on a simple principle: “never trust, always verify.” Unlike traditional security models that focus on defending the perimeter, Zero Trust assumes potential breaches and verifies every access request regardless of source. The good news? You don’t need enterprise-level resources to implement these critical protections for your business.
This guide will walk you through affordable, practical steps to strengthen your security posture using Zero Trust principles without breaking the bank.
Understanding Zero Trust Security
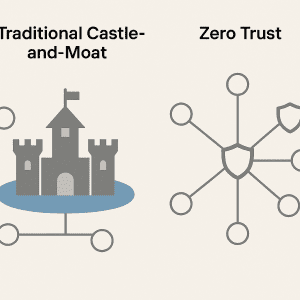
At its core, Zero Trust security embraces three fundamental principles:
- Verify explicitly: Authenticate and authorize based on all available data points, including user identity, location, device health, service, and workload.
- Use least privilege access: Limit user access with Just-In-Time and Just-Enough-Access to minimize exposure.
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to improve defenses.
Unlike traditional security approaches where anything inside your network is trusted, Zero Trust recognizes that threats can come from both outside and inside your organization. Research from IBM’s Security Cost of a Data Breach Report shows that businesses implementing Zero Trust principles experienced breach costs 35% lower than those without such protections.
For small businesses, implementing Zero Trust isn’t just about security—it’s about business continuity, customer trust, and competitive advantage. Our cybersecurity services help North Texas businesses build robust security frameworks tailored to their specific needs and budgets.
Assessing Your Current Security Posture

Before implementing Zero Trust, you need to understand your current security landscape. Start by asking these critical questions:
- What are your most valuable data assets?
- Which systems and applications access this data?
- Who needs access to these resources?
- What security measures are currently in place?
- Where are your biggest security vulnerabilities?
This assessment doesn’t require expensive consultants. Many organizations can utilize free tools like Microsoft Secure Score or the CISA’s Cyber Security Evaluation Tool (CSET®) to evaluate their security posture.
At RZR Solutions, we offer complimentary initial security assessments for small businesses, helping you identify critical gaps without a significant upfront investment. Understanding your current position is the first step toward implementing targeted, cost-effective security improvements.
Foundational Elements of Budget-Friendly Zero Trust
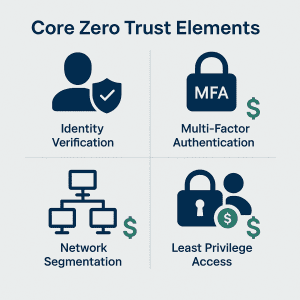
Building a Zero Trust framework doesn’t require implementing everything at once. Start with these foundational elements that provide maximum security value at minimal cost:
1. Strong Identity Management
The cornerstone of Zero Trust is knowing who is accessing your resources. Implementing strong identity management doesn’t necessarily require expensive new systems—many small businesses can leverage identity capabilities already included in their Microsoft 365 subscriptions.
2. Multi-Factor Authentication (MFA)
MFA is perhaps the single most cost-effective security measure you can implement, preventing 99.9% of account compromise attacks according to Microsoft. Many services offer MFA capabilities at no additional cost, including popular platforms like Microsoft 365, Google Workspace, and most major banking and SaaS applications.
3. Network Segmentation
Dividing your network into smaller, isolated segments prevents attackers from moving laterally if they breach one area. This can often be accomplished using features already available in your existing networking equipment or through properly configured VLANs.
4. Principle of Least Privilege
Restricting access rights to the minimum necessary to perform job functions costs nothing but time to implement. Start by auditing current access levels and scaling back unnecessary permissions—a process our compliance team can help streamline.
These foundational elements provide the security backbone for your Zero Trust implementation without requiring significant capital investment. Many small businesses already have the tools needed; they just need proper configuration and management.
Phase 1 Implementation Steps

Your Zero Trust journey begins with these practical first steps that deliver immediate security benefits without overwhelming your resources:
Enable MFA Everywhere Possible
Start with your most critical systems—email, financial applications, customer data repositories, and remote access. Most modern business applications offer free MFA options:
- Microsoft 365 includes basic MFA features in all business plans
- Google Workspace provides free authentication app options
- Many banking and accounting platforms offer free SMS or app-based verification
Our managed IT services include MFA deployment and user training to ensure smooth adoption across your organization.
Implement Basic Network Segmentation
Even with limited hardware, you can create logical boundaries:
- Separate guest Wi-Fi from your business network
- Create distinct VLANs for different departments or functions
- Isolate legacy systems or IoT devices that can’t be fully secured
Simple segmentation dramatically reduces your attack surface with minimal cost. Proper network monitoring ensures these segments remain secure over time.
Review and Adjust Access Controls
Audit who has access to what in your organization:
- Remove administrative privileges from everyday user accounts
- Implement role-based access for applications and data
- Regularly review permissions, especially after role changes
According to the Ponemon Institute, over 60% of small businesses that experienced a breach cited inappropriate access privileges as a contributing factor. Our team can help implement proper access controls aligned with industry best practices.
Begin Password Management Improvements
Strengthen your first line of defense:
- Implement a password manager for your team (many offer affordable small business plans)
- Establish and enforce strong password policies
- Remove shared passwords for business applications
These Phase 1 steps establish your Zero Trust foundation without significant expenditure. Many can be implemented with your existing infrastructure by leveraging free or low-cost tools and capabilities already included in your current services.
Phase 2 Implementation Steps

Once you’ve established your foundation, these next steps enhance your Zero Trust implementation:
Data Classification and Protection
Not all data requires the same level of protection. Implementing basic data classification helps focus your security efforts:
- Identify and label sensitive information (customer data, financial records, intellectual property)
- Apply appropriate controls based on sensitivity
- Consider affordable data loss prevention tools included in services like Microsoft 365 Business Premium
Our data protection specialists can help design classification schemes that balance security with usability.
Endpoint Protection Enhancement
Secure all devices accessing your network with these affordable approaches:
- Deploy modern antivirus/anti-malware with behavior-based detection
- Implement endpoint protection policies (disk encryption, auto-updates, application controls)
- Consider Microsoft Defender for Business (included in some Microsoft 365 plans) or other cost-effective solutions
The FBI’s Internet Crime Complaint Center reported that businesses without adequate endpoint protection were 3x more likely to suffer ransomware attacks—a risk no small business can afford.
Cloud Security Optimization
Many cloud platforms include powerful security features at no extra cost:
- Enable security defaults in Microsoft 365 and similar platforms
- Configure cloud app security policies
- Implement conditional access rules based on device, location, and risk
Our cloud services team specializes in optimizing security settings across popular platforms, ensuring you utilize all available protections without additional licensing costs.
Basic Security Monitoring
Maintain visibility into your environment:
- Enable built-in logging features in your existing systems
- Set up basic alerts for suspicious activities
- Establish regular security review processes
Even without enterprise SIEM solutions, basic monitoring provides crucial early warning of potential breaches. Combine this with our professional monitoring services for comprehensive protection.
Common Challenges and How to Overcome Them

Implementing Zero Trust isn’t without challenges, especially for resource-constrained small businesses:
Employee Resistance
Security changes often face resistance when they’re perceived as hindering productivity:
- Solution: Start with clear communication about why changes are necessary
- Solution: Implement changes gradually with appropriate training
- Solution: Gather feedback and adjust implementation where possible
Our team provides user-friendly training resources and change management support to ensure smooth adoption.
Technical Complexity
Limited IT expertise can make Zero Trust seem overwhelming:
- Solution: Focus on user-friendly solutions with good documentation
- Solution: Leverage cloud-based security tools with simplified management
- Solution: Consider managed security services for complex components
Budget Constraints
Financial limitations are real for small businesses:
- Solution: Prioritize based on risk assessment results
- Solution: Fully utilize security features already included in your existing services
- Solution: Consider security-as-a-service options with predictable monthly costs
According to the Small Business Administration, 60% of small companies go out of business within six months of a cyberattack. Investing strategically in security is not just an expense—it’s business insurance.
Balancing Security and Usability
Overly restrictive controls can impact productivity:
- Solution: Start with higher-risk areas and gradually expand
- Solution: Test changes with pilot groups before full deployment
- Solution: Collect user feedback and make reasonable adjustments
At RZR Solutions, we believe security and productivity should complement rather than compete with each other. Our approach balances protection with practicality.
Free and Low-Cost Tools to Consider
These affordable tools can dramatically enhance your security posture:
Identity and Access Management
- Microsoft Azure AD Free/Basic: Included with Microsoft 365 subscriptions
- Google Workspace: Basic identity management included in all plans
- Bitwarden Teams: Affordable password management for small businesses
Endpoint Protection
- Microsoft Defender for Business: Included in Microsoft 365 Business Premium
- Sophos Home Premium: Commercial-grade protection at consumer prices
- Bitdefender GravityZone Business Security: Affordable SMB-focused solution
Network Security
- pfSense: Free, open-source firewall/router software
- OPNsense: Business-friendly open-source security platform
- Wireshark: Free network protocol analyzer for monitoring traffic
Security Assessment
- Microsoft Secure Score: Free security assessment tool for Microsoft environments
- CISA’s Cyber Security Evaluation Tool: Free comprehensive assessment tool
- OpenVAS: Open-source vulnerability scanner
Strategic implementation of these tools, combined with our technology expertise, provides enterprise-grade protection without enterprise-level costs. We can help you select and configure the right mix of solutions for your specific needs and budget.
Creating a Roadmap for Ongoing Implementation
Zero Trust implementation is a journey, not a destination. Create a sustainable roadmap with these steps:
Set Realistic Timelines
Break your implementation into manageable phases:
- Phase 1 (Months 1-3): Foundation building (MFA, basic access controls)
- Phase 2 (Months 4-6): Enhanced protection (endpoint security, data classification)
- Phase 3 (Months 7-12): Maturity (monitoring improvements, advanced policies)
Measure Effectiveness
Track your progress with these key metrics:
- Security incident frequency and severity
- User adoption rates of security measures
- Risk assessment scores over time
- Compliance posture improvements
Plan for Gradual Expansion
As your security matures and budget allows:
- Expand monitoring capabilities
- Implement more sophisticated conditional access policies
- Add automated response capabilities
- Consider managed detection and response services
Our custom application development can help integrate security measures into your unique business workflows for seamless protection.
Budget Planning for Future Investments
As your business grows, plan for strategic security investments:
- Allocate a percentage of IT budget specifically for security
- Consider security-as-a-service models for predictable costs
- Evaluate cyber insurance for residual risk
Working with RZR Solutions provides access to enterprise-grade security expertise at small business-friendly rates, helping you maximize protection while optimizing costs.
Conclusion: Securing Your Business Without Breaking the Bank

Implementing Zero Trust security doesn’t require enterprise resources or massive budgets. By taking a phased, strategic approach focused on the highest-impact elements, small businesses can significantly improve their security posture without breaking the bank.
Remember these key takeaways:
- Start with the foundational elements: identity, MFA, access controls
- Leverage security features already included in your existing services
- Focus on your highest-risk areas first
- Create a sustainable implementation roadmap
- Consider managed security services to fill expertise gaps
At RZR Solutions, we specialize in helping North Texas small businesses implement robust security frameworks that balance protection with practicality. Our team understands the unique challenges facing small businesses and provides tailored solutions that maximize security within your budget constraints.
Ready to strengthen your security posture with affordable Zero Trust implementation? Contact us today for a complimentary security assessment and learn how we can help protect your business without overwhelming your resources.
Bonus: Zero Trust Implementation Checklist

Download our free Zero Trust Implementation Checklist to track your progress and ensure you’re covering all critical areas of protection. This practical resource helps you methodically strengthen your security posture while staying within budget constraints.
Have questions about implementing Zero Trust on a budget? Reach out to our team for personalized guidance tailored to your business needs.